Install driver by helm
helm repo add aws-efs-csi-driver https://kubernetes-sigs.github.io/aws-efs-csi-driver/
helm repo update aws-efs-csi-driver
helm upgrade --install aws-efs-csi-driver --namespace kube-system --set useFips=true aws-efs-csi-driver/aws-efs-csi-driverCreate storage class for EFS
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: efs
provisioner: efs.csi.aws.comusing in pv-pvc for deployment
kind: PersistentVolume
apiVersion: v1
metadata:
name: pv-name
spec:
capacity:
storage: 5Gi
volumeMode: Filesystem
accessModes:
- ReadWriteMany
persistentVolumeReclaimPolicy: Retain
storageClassName: efs
csi:
driver: efs.csi.aws.com
volumeHandle: fs-id
---
kind: PersistentVolumeClaim
apiVersion: v1
metadata:
name: pvc-name
spec:
accessModes:
- ReadWriteMany
storageClassName: efs
resources:
requests:
storage: 5G
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-test
labels:
name: nginx-test
spec:
replicas: 2
selector:
matchLabels:
app: nginx-test
template:
metadata:
labels:
app: nginx-test
spec:
containers:
- name: nginx-test
image: nginx
ports:
- name: nginx-test
containerPort: 80
volumeMounts:
- name: nginx-share-html
mountPath: /usr/share/nginx/html
volumes:
- name: nginx-share-html
persistentVolumeClaim:
claimName: pvc-name
Check VPC of EFS and EKS
VPC for EKS and EFS must be in the same zone
EFS > EFS detail > network tab > manage button: set security groups = security groups of EKS for each availability zone of VPC

EKS > EKS detail > Networking tab
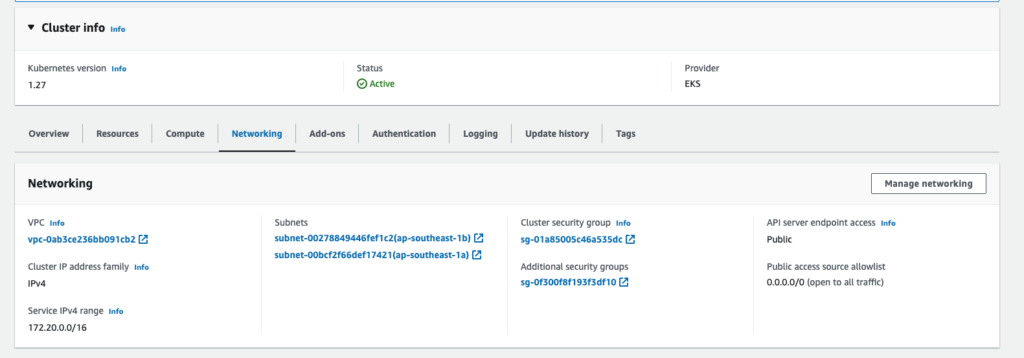
Check permission of role AmazonEKS_EFS_CSI_DriverRole
IAM > roles > check name AmazonEKS_EFS_CSI_DriverRole , if not exist, create new one with that name > custom trust policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::325273135247:oidc-provider/oidc.eks.ap-southeast-1.amazonaws.com/id/3E9DA335656DBC0E209DC5783E632416"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringLike": {
"oidc.eks.ap-southeast-1.amazonaws.com/id/3E9DA335656DBC0E209DC5783E632416:sub": "system:serviceaccount:kube-system:efs-csi-*",
"oidc.eks.ap-southeast-1.amazonaws.com/id/3E9DA335656DBC0E209DC5783E632416:aud": "sts.amazonaws.com"
}
}
}
]
}Remember change OIDC link with current EKS OIDC link provide in EKS detail and change iam number
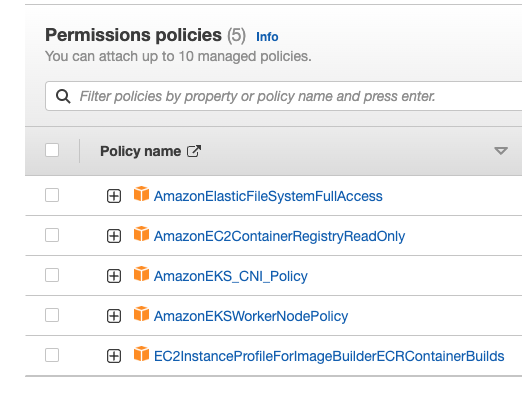
Check permission of role eks-node-worker
create role name eks-node-worker with these policies
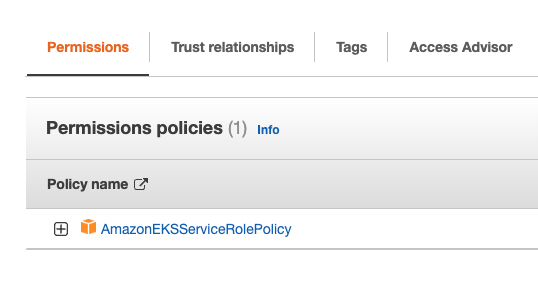
The same way above, check role AWSServiceRoleForAmazonEKS
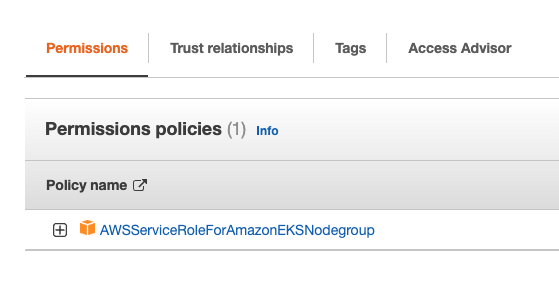
AWSServiceRoleForAmazonEKSNodegroup
eksClusterRole
